Figure SE.00 - Security Overview : Class diagram
| Created: | 3/28/2022 3:51:09 PM |
| Modified: | 6/13/2022 6:32:43 PM |
 Project: Project: |
|
 Advanced: Advanced: |
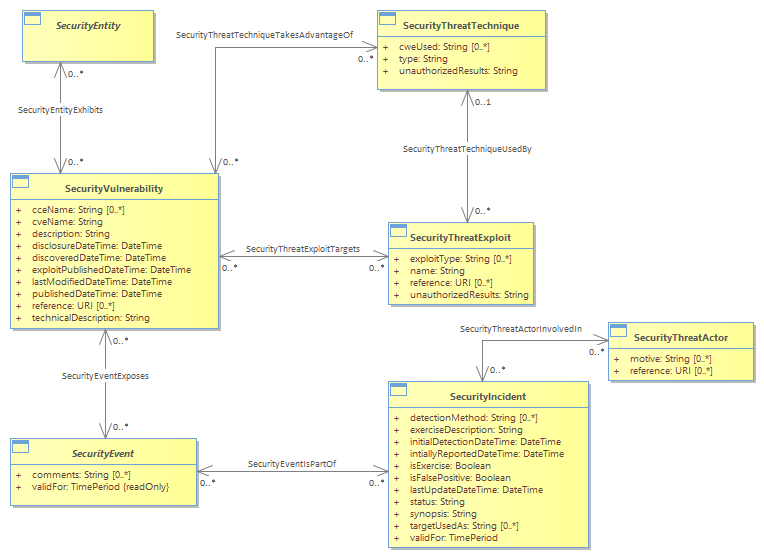
<b>Security Domain</b><br/>When incorporating key Security Management concepts into the SID model, the modelers focused on the five primary concepts: assets, threats, vulnerabilities, events, and incidents, related information, and their relationships. <br/>Security was added to the Enterprise Risk area of the SID because of their very nature. Each entity was qualified by the name “Security” to distinguish these types of entities as specific to Security. For example, there are other types of entities that deal with Incidents and Events.<br/>Also, the Device (Asset) entity was generalized to accommodate Vulnerabilities, Threats, Events, and Incidents associated with any type of SID entity, such as Services, Products, and other types of Resources, such as connections.<br/>The key entities actually represent groups of entities. Therefore, they were added as ABEs. <br/><b>Overview of Security</b><br/>When incorporating key Security Management concepts into the SID model, the modelers focused on the five primary concepts: assets, threats, vulnerabilities, <br/>The following entities are core to the security model: <br/>SecurityEntity: Used to describe any asset that exposes security related vulnerabilities, and has the potential for security related events. <br/>SecurityVulnerability: Potential weakness that may be exploited by an adversary or threat.<br/>SecurityThreatExploit and SecurityThreatTechnique: Threats represent entities and characteristics of entities that may maliciously or non-maliciously exploit vulnerabilities.<br/>SecurityThreatActor: Use “techniques” such as social engineering, or phishing to maneuver assets into positions where they can use “exploits” to take advantage of weaknesses to gain access or information that is either inherently valuable, or can be used to gain further access.<br/>SecurityEvents and SecurityIncidents: Incidents and events are recorded and reported. The primary difference is that incidents result from assessment(s) of event(s).<br/>SecurityIncidentImpact: Supports information such as, how the incident was allowed to happen, what threat actor caused it, and how “bad” the damage is. <br/>The model shows that a Security Entity, such as a network element, exhibits Vulnerabilities, which may be taken advantage of by a Security Threat Technique, specifically targeted by a Security Threat Exploit. A Security Event exposes the e Vulnerability and may result in a Security Incident being created to resolve and fix the Vulnerability.<br/>