Figure SE.08 - Security Threat Basic Entities : Class diagram
| Created: | 3/28/2022 3:51:09 PM |
| Modified: | 6/13/2022 4:02:39 PM |
 Project: Project: |
|
 Advanced: Advanced: |
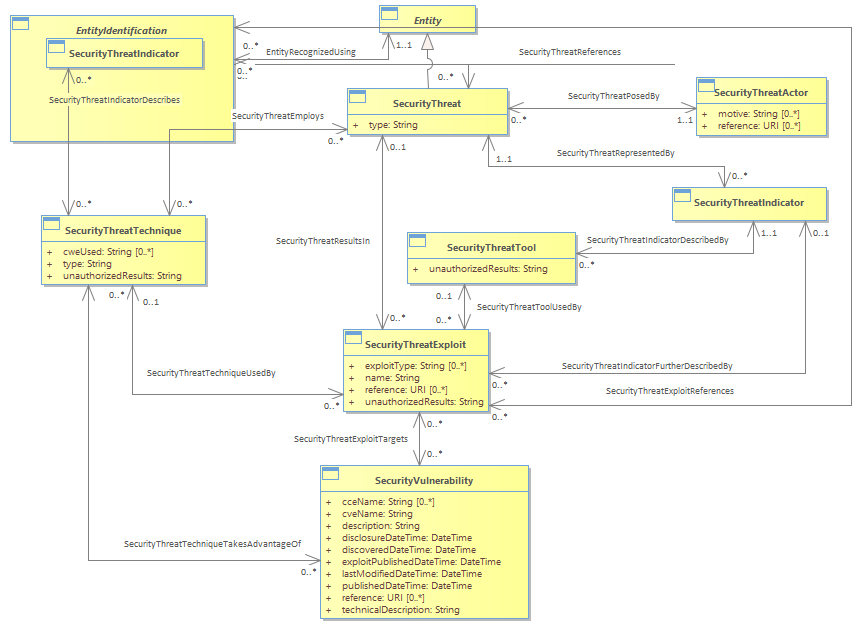
The vulnerability portion of the model is designed to carry information about potential weaknesses in hardware, applications, and operating systems that may be exploited by an adversary or threat. (The original contribution was designed around the NIST National Vulnerability Database (NVD) and tools.) <br/>The threat area of the model is constructed to represent entities and characteristics of entities that may maliciously or non-maliciously exploit vulnerabilities on network-connected devices.<br/>Much of the information in the threat model describes elements that commonly trigger signatures or algorithms for detecting malicious code or behaviors. In order to better understand the threat environment, it’s necessary to be aware of common attacks that are being attempted. Summaries of events, which may represent successful and unsuccessful attacks against systems and incident reports that report successful compromises, are required. <br/><b>Threat Actor </b><br/>At its highest level, a Security Threat Actor can be a person, an organization, or a tool that has been created and released onto networks, but no longer has any relationship with its original creator. As can be inferred, organizations can be made up of subordinate organizations and/or people. Both organizations and people can use tools, so any given threat can be composed of organizations, people, and tools. <br/><b>Threat Indicators </b><br/>At its highest level, the ability to detect and describe threats is key to the vast majority of use cases for the threat model. To support the ability to detect threats, a large part of the threat model deals with describing “indicators” of threat activity or presence. Indicators of specific threat actors or general threat activity range from commonly used threat IP connection endpoints, to dynamic and static DNS names, to indicators showing commonly used techniques such as suspicious email attachments, SQL injections, known malicious PKI certificates, and others. Other threat indicators may be related to suspicious traffic that is generally prohibited on networks.<br/><b>Threat Techniques </b><br/>At its highest level The Threat Actors can use “techniques” such as social engineering, or phishing to maneuver devices and/or network users into positions where they can use “exploits” to take advantage of weaknesses the victim has to gain access or information that is either inherently valuable, or that can be used to gain further access. <br/><b>Threat Tools</b><br/>Organized and distributed software that can be used to attack an IT resource or service. Threat tools include viruses, botnets, and other software that enables or automates a threat actor’s attack.<br/><b>Threat Exploit</b><br/>A threat exploit takes advantage of a vulnerability to gain access or cause an adverse effect.<br/>