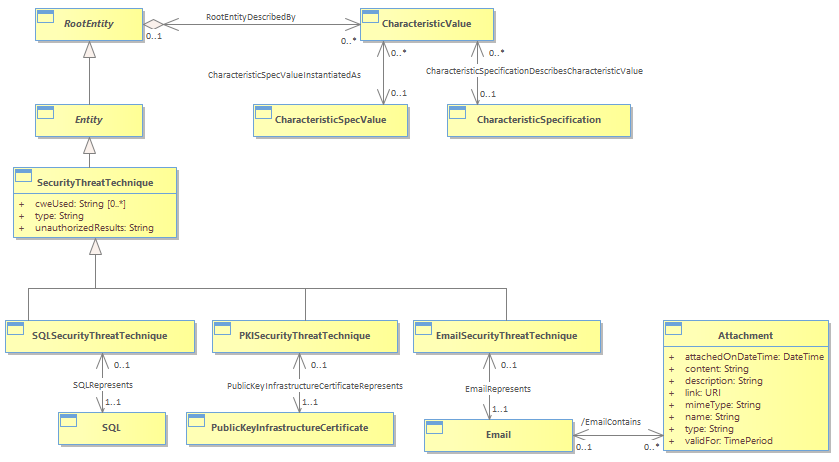
Figure SE.09 - Security Threat Technique : Class diagram
| Created: | 3/28/2022 3:51:09 PM |
| Modified: | 6/13/2022 4:00:54 PM |
 Project: Project: |
|
 Advanced: Advanced: |
A threat actor may use multiple techniques to exploit a vulnerability on an IT resource. The existing Security Threat ABE pre-defines a few threat techniques, namely SQL, such as a SQL injection attack, PKI, such as spoofing a PKI certificate, and email, including phishing, social engineering, and malicious code attachments. <br/>