Figure DI.01 & DI.02-I01 - Digital Identity overview & Credential Hierarchy

|
Project:
|
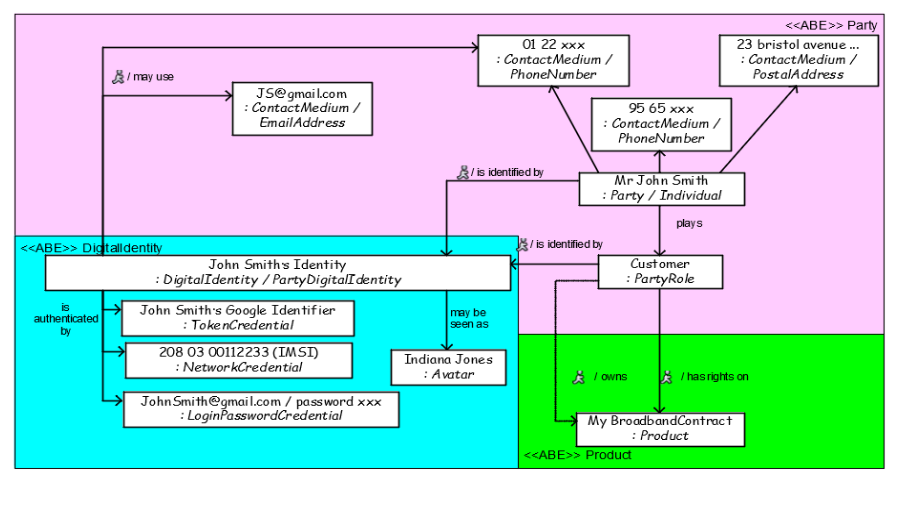
Figure DI.01 & DI.02-I01 - Digital Identity overview & Credential Hierarchy : Object diagram
<font color="#29313b">Context: </font><br/><ul>
<li><font color="#29313b">John Smith plays the role of Customer for My Broadband Contract and therefore he has rights on it. </font></li><li><font color="#29313b">John Smith declared three ContactMedium to THE csp to allow to interact with him</font></li></ul> <font color="#29313b">To allow John Smith to exercise his rights (without direct interactions with people from the CSP, through Web for example), a DigitalIdentity has been created for John Smith. JS’s DigitalIdentity is owned by John Smith and identifies his Customer PartyRole</font><br/><font color="#29313b">John Smith declared on his DigitalIdentity two ContactMedium. These ContactMedium can be different from the one he declared to the CSP and cannot be used by the operator’s marketing. One of them can be used to send password in case of forgetting.</font><br/><font color="#29313b">John Smith has automatically 2 Credentials to identify / authenticate:</font><br/><ul> <li><font color="#29313b">a LoginPasswordCredential: that must be explicitly typed by John Smith on the Web for example</font></li><li><font color="#29313b">A NetworkCredential using his mobile’s IMSI that can be automatically identified when he interacts with the CSP.</font></li></ul> <font color="#29313b">Later John Smith has declared a TokenCredential from google that allows JS not to have to identify / authenticate again when he already has been identified / authenticated by google.</font><br/><font color="#29313b">John Smith chooses to be seen as “Indiana Jones” when he connects on the web.</font><br/> |


