Figure LR.16-I01 - Illustration – A Simple 2547bis MPLS VPN

|
Project:
|
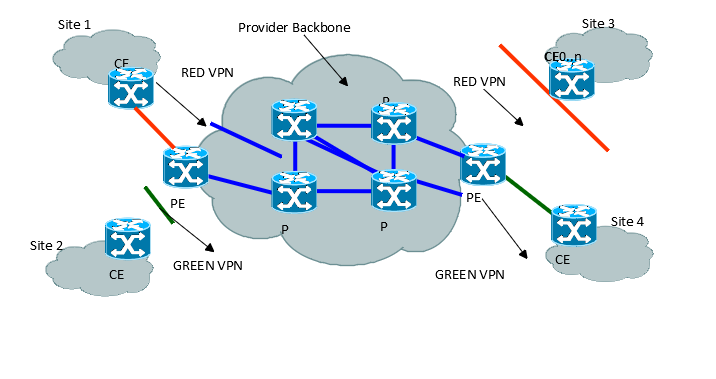
Figure LR.16-I01 - Illustration – A Simple 2547bis MPLS VPN : Object diagram
<font color="#e0121d">Roles in More Detail</font><br/><font color="#29313b">Now that all of the major business entities for Resource and LogicalResource have been explained, we can return to examining the use of Roles to abstract application functionality. For example, consider a 2547bis MPLS VPN. No matter how complicated the topology of the VPN, there are basically three roles that a device can play in this scenario:</font><br/><ul>
<li><font color="#29313b">CustomerEdge (CE) – represents a router that connects the Customer’s traffic to the VPN</font></li><li><font color="#29313b">ProviderEdge (PE) – represents a router at the edge of the VPN to which a CE router can connect to</font></li><li><font color="#29313b">Provider (P) – represents a router in the core of the VPN that does not connect to a CE router</font></li></ul> <font color="#29313b">The basic VPN topology is shown in Figure LR.16 - Illustration – A Simple 2547bis MPLS VPN</font><br/><font color="#29313b"><br/></font><font color="#29313b">The Figure below shows two VPNs. The “Red” VPN connects Sites 1 and 3 through the Provider backbone, while the Green VPN connects Sites 2 and 4 through the same Provider backbone. Note that these are two distinct VPNs that share a common network. The concept of Roles can be used with other parts of this model to standardize (for example) how CE routers connect to PE routers, as well as how traffic is forwarded. For example, a set of policies could be defined that determine the specific characteristics and behavior that a particular CE router will have, which could be used to constrain the protocols used controlling how it connects to different types of PE routers. Abstracting this functionality using roles enables policies to be independent of any specific device, facilitating redundancy and reuse. </font><br/><font color="#29313b">First, note that the core of the Provider Backbone is represented by routers that play the same Role (Provider). This enables us to differentiate their configuration from the PE and CE routers shown in Figure LR.49 above. More importantly, it means that these four routers are functionally equivalent, and once a basic template is developed to configure one, it can be applied (with simple modifications to parameterize device-specific attributes, such as name and IPAddress) to the other P routers.</font><br/><font color="#29313b">This is also true of the configurations of the PE and CE routers.</font><br/><font color="#29313b">Roles imply innate functionality provided by the entity playing that role which is not provided by other entities. For example, a Router playing the CE role is solely responsible for connecting the Customer to the VPN. A router playing the PE role is solely responsible for exercising import routing policies, which are used to determine whether a remote route transmitted by a CE should be installed and propagated in the VPN or not. PE roles do not connect to the Customer, and CE roles do not import routing policies.</font><br/><font color="#29313b">This description of Roles is at a device level – it can involve using roles to describe physical as well as logical aspects of the device. Thus, while we have been describing LogicalResourceRoles, we could just as easily describe PhysicalResourceRoles, or even combine the two to describe CompoundResourceRoles (which would help determine the overall behavior of a CompoundResource, such as a router).</font><br/><font color="#29313b">Just as a CompoundResource was defined as a mechanism to aggregate PhysicalResources as well as LogicalResources, a CompoundResourceRole can aggregate PhysicalResourceRoles as well as LogicalResourceRoles. For example, a Service Provider could decide that only certain type of connections using a particular type of media (e.g., Serial) will be supported between the CE and the PE routers. Therefore, any router playing either the CE or the PE roles must support serial connectivity. Furthermore, since the P routers are forwarding traffic in the core of the Service Provider backbone and not concerned with Customer connectivity, there is no reason for them to support serial connectivity (for connecting to Customers). Thus, roles can be used to help determine what types of PhysicalResources (e.g., Protocols) and LogicalResources (e.g., Line Cards) are used on to realize functionality required by a CompoundResource. As a simple example, since a P router just connects to other P routers and PE routers, its configuration must ensure that routes aren’t leaked across the PE routers to CE routers. Thus, the role of the P router differentiates its function from the CE and PE routers.</font><br/> |



